🔐 Why Signing Git Commits Matters
Git allows anyone to spoof a committer name or email with just a few commands:
git config user.email "bill.gates@microsoft.com"
git commit -m "Add tractor autopilot mode."
This opens the door for impersonation and codebase hijacking. To avoid this, developers should sign their commits using a cryptographic key pair. This adds a digital signature, giving commits a "Verified" badge on GitHub, confirming that the code genuinely came from the stated author.
🚀 Easier than Ever with SSH Keys
Previously, commit signing required generating and managing GPG keys, a cumbersome and outdated method. Today, GitHub supports commit signing with SSH keys, making the process significantly easier, especially for teams already using SSH for code pushes.
Now you can sign commits and get the same verified badge in seconds, no GPG headaches required.
🧩 Signing Commits: Two Options
You can sign Git commits using either GPG or SSH keys. Here's how to set up both:
🔑 Option 1: GPG
🛠️ Generate a GPG Key on Windows
Follow GitHub’s official guide to generate a GPG key in Git Bash. Then export and import the key into Kleopatra, the GUI tool included in Gpg4win, to use it with external tools like Visual Studio.
gpg --export-secret-key > private.key
If you have multiple keys, specify the key ID explicitly.
⚙️ Import into Kleopatra
Open Kleopatra
Import
private.keyConfirm the key appears in the list
🔁 Enable Automatic Signing
To avoid manually signing each commit, set these Git configurations:
git config --global user.signingkey <key-id>
git config --global commit.gpgsign true
🧠 VS Code Users (on Windows)
You must also configure Git to use the GPG program:
git config --global gpg.program "C:\Program Files (x86)\GnuPG\bin\gpg.exe"
🔐 Option 2: SSH
SSH commit signing is simpler for most developers:
📦 Requirements
Git 2.34.0 or later
An existing SSH key (or generate a new one)
⚙️ Setup Steps
Go to GitHub SSH Settings
Click "New SSH Key"
Choose "Signing Key" as the key type
Paste your SSH public key
Then configure Git:
git config --global gpg.format ssh
git config --global user.signingkey <your-ssh-key>
git config --global commit.gpgsign true
You can now sign commits and tags using -S and -s flags:
git commit -S -m "Fix security vulnerability"
🔍 Verify Signed Commits
To check if commits are signed:
git log --show-signature
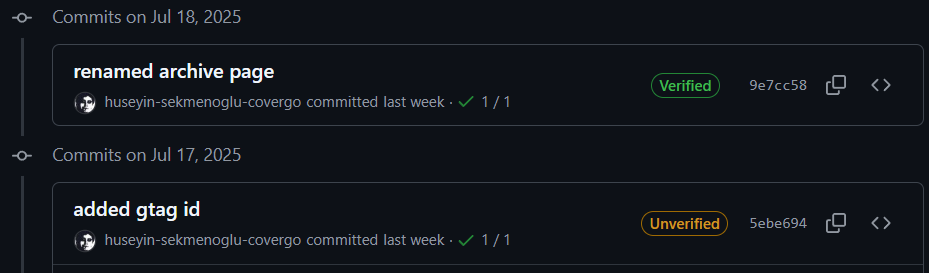
💡 Tip: Use Signing in All Tools
Whether you're using Visual Studio, VS Code or JetBrains Rider make sure the tool is configured to use your key for signing.
✅ Summary
Method | Best For | Required Tools |
|---|---|---|
GPG | Advanced workflows, cross-platform signing | Gpg4win, Kleopatra |
SSH | Simplicity, GitHub users already using SSH | Git 2.34+, GitHub |
Signing commits boosts your codebase's security and adds professionalism. Now that SSH signing is easier than ever, there's no reason not to start verifying your commits today.